What is NetIQ Privileged Account Manager - User Access Audit?

A privileged user is someone who has special access to your internal system, but how about if that privileged user is no longer your business partner or someone inside your company?
Most information breaches happen from misuse of privileged account. That is why PAM is being built. PAM keeps your company safe from accidental misuse of privileged access. The bigger and more complex your company’s IT system, the more privileged users and risk of leak that you have.
PAM helps you to control and monitor privileged account access. It allows privileged users to work on systems without exposing administrator or supervisor password, and takes on record of every privileged account activities.
What would you get by purchasing this product?
Easy Drag-and-Drop Rule Creation
![]()
The system will make everything easier, with simpler drag-and-drop rule creation process, our PAM virtually eliminates the need of manual scripting.
Integrated test-suite tool also allows you to test the effectiveness of the new rule combinations that you’ve created.
User Command Configuration
![]()
As an admin, you can configure every policies to allow or deny user activity based on “who, what, where, when”, Basically your administrator will control what each users are authorized to do at what time and from what location.
Risk-Analysis Engine
![]()
PAM continuously analyze potential risk to provide an early detection if there is any risky action happens in real-time as it is typed.
All action are assigned with risk level of 0 to 9 based on executed command, user profile, and location. High risk command are red color coded with varying shade for easier auditor inspection.
Automated Session Termination & Access Revocation
![]()
In the event of risk-based activity PAM will deliver automated policy enforcement. Admin may configure the PAM to automatically disconnect a high-risk activity session or revoke the detected user from accessing any privileged accounts.
Auditing and Reporting
![]()
PAM is capable to audit all user activity with 100% keystroke log & video capture feature. PAM provides recording & reporting for a variety of access-grant activities that helps you to take a legal action with the cyber crime records.
Here is the detailed features you will get
01. Thorough Privileged Account Management
By using this feature, you are able to safely grant users with only the privileges they need, when they actually need it.
PAM delivers privileged user control, tracking and auditing for all credential system, including:
- Applications (e.g. SAP System)
- Database (e.g. Microsoft SQL database, Oracle DBMS)
- UNIX, Linux, and Windows platforms
- Cloud services (e.g. Salesforce.com)
- Virtual servers (e.g. VMWare ESXi)
Your company app will be secured by controlling what commands users are granted to run, at what time, and from where. Complete with automatic recording on all user activities, if something wrong happens, you can quickly identify suspicious activity and take immediate action to prevent their next moves.
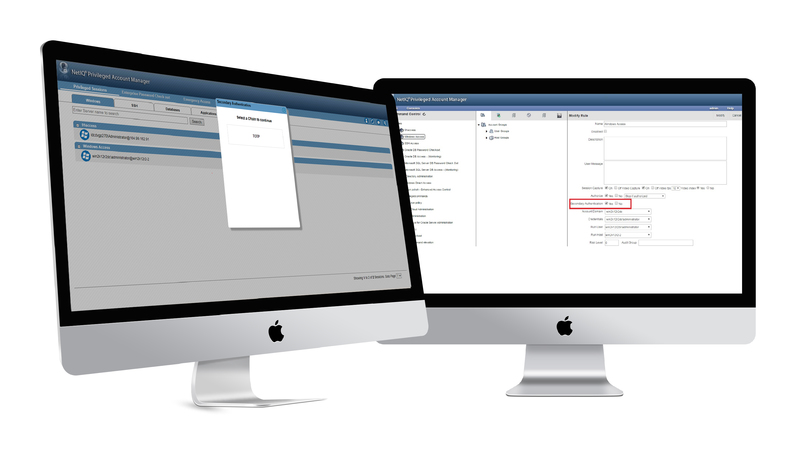
02. Advanced Privileged Accounts Authentication
PAM integrates with advanced authentication solution to build layer of defenses. Design your step-up authentication upon the access policies that you define, request multiple-authentication factors for access to sensitive system resources & assets.
PAM enables you to leverage your authentication methods, including:
- One time passwords (OTP)
- Smartphones
- Voice
- SMS (e.g. text)
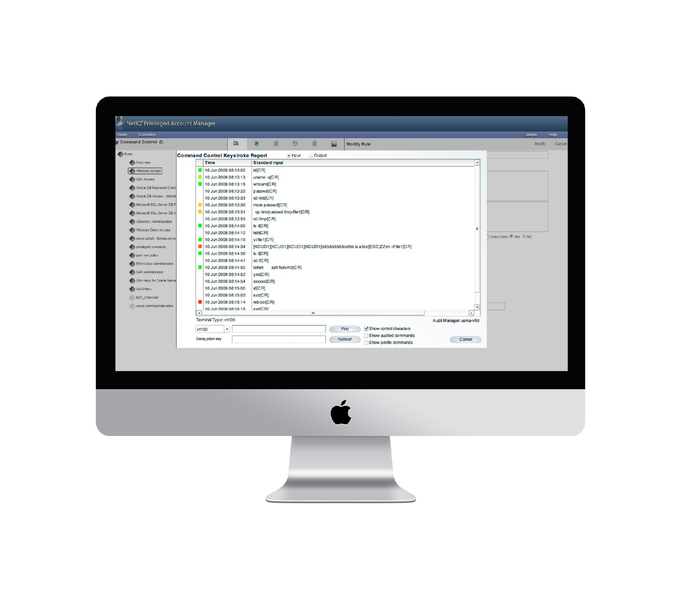
03. Risk-based Session Control
PAM enables you to identify and analyze potential risk before it negatively impact your business. With unique risk-analysis engine, PAM analyzes & categorize each command with risk level 0 to 9.
If an event require further analysis, it is escalated to appropriate managers either through email / event flag on the console; to then take immediate action. PAM are also equipped with automated access restriction, based on your policy.

04. Database Privileged Account Monitoring
PAM provides user access monitoring for enterprise-critical database such as Oracle & Microsoft SQL. Monitor the command of administrator that is running against your database and receive real-time analysis of the command in the same time. As this is an agent-less operation within the database, there is no impact to the database’s performance.
05. Secured Password Vaulting
Store your credential, key, and secret information in PAM’s Enterprise Credential Vault. It helps you to manage your company’s privileged accounts and grant privileged users to check-out and return passwords, and supports both policy-based and workflow-based password retrievals.
Some of the other features are:
- Check-out credentials for a custom duration of time
- Out-of-the approval workflow and notifications
- Broader privileged account support
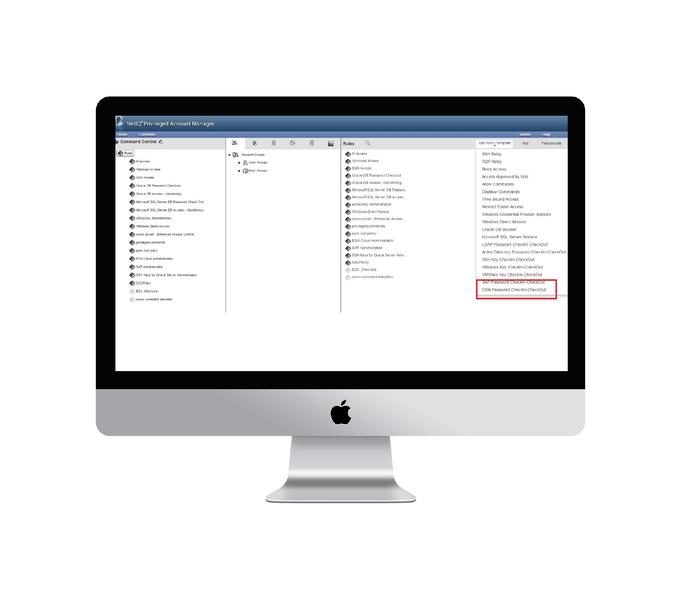
Product Specification Sample
PAM Product
- Privileged Account Manager Module Add-on
(per managed endpoint) - Privileged Account Manager Add-on Initial total Care (per managed endpoint)
Base Platform
- Identity & Access Management Base License
(per affiliated/enterprise entity) - Identity & Access Management Base Initial Total Care (per affiliated/enterprise entity)
Local Service and Support
-
Standard PAM installation only*
- Service support 8×5, 4 Troubleshoot Tickets and 4 Health Checks, 1 Year
* Restrict to vault setup and policies setting.
No customization of connectors to target servers

